OWASP Find Security Bugs
Find Security Bugs is the SpotBugs plugin for security audits of Java web applications.
Website : http://find-sec-bugs.github.io/
Main developers
Notable contributions
- David Formánek
- Major improvements and refactoring on the taint analysis for injections.
- The creation of a detector for hard coded passwords and cryptographic keys.
- Tomáš Polešovský
- Improvements and bug fixes related to the taint analysis.
- Maxime Nadeau
- New detectors surrounding the Play Framework and improvements related to Scala.
- Naoki Kimura
- Detector for injection in custom API
- Translation of messages in Japanese
- Dave Wichers
- Improvement to vulnerability descriptions
Project Sponsors
The development of Find Security Bugs is supported by GoSecure since 2016. The support includes the development of new detectors and the research for new vulnerability classes.
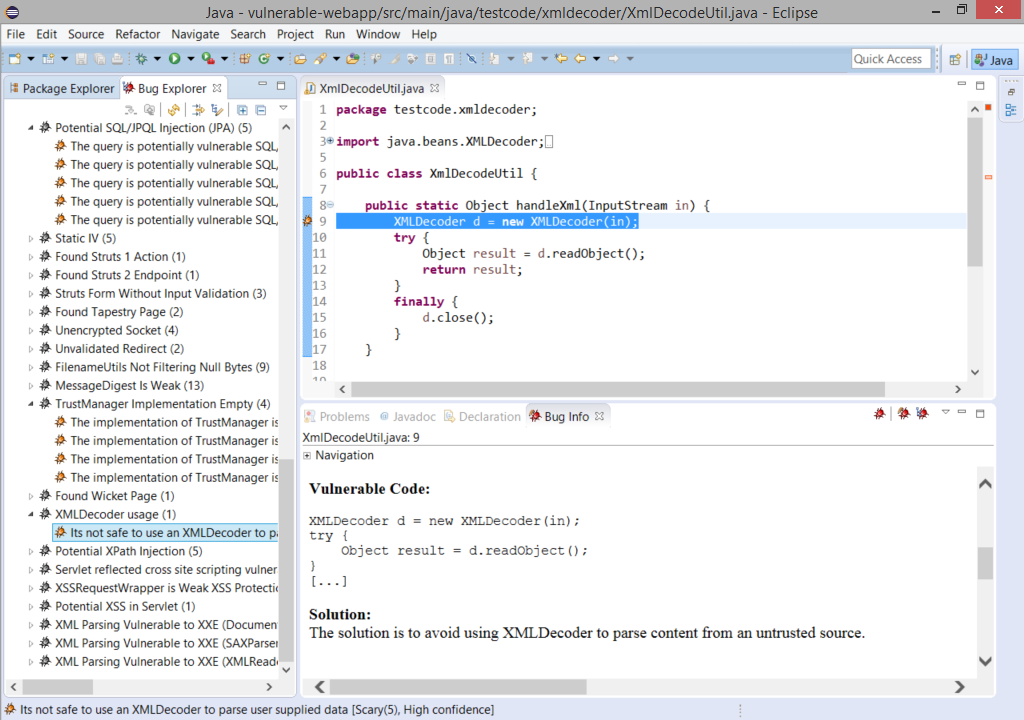
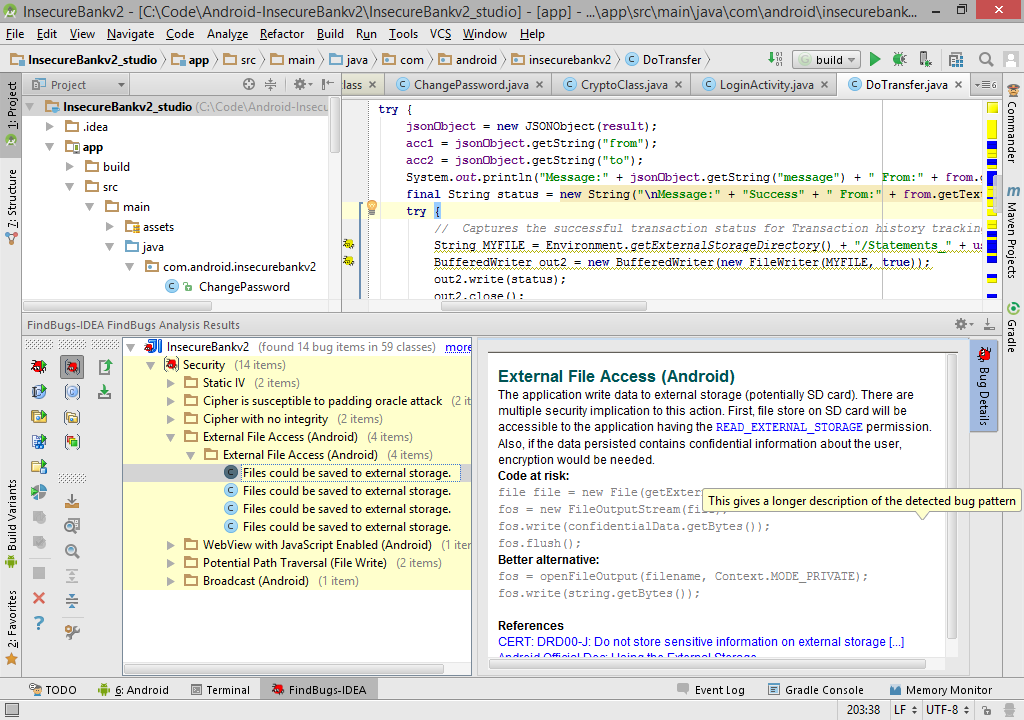
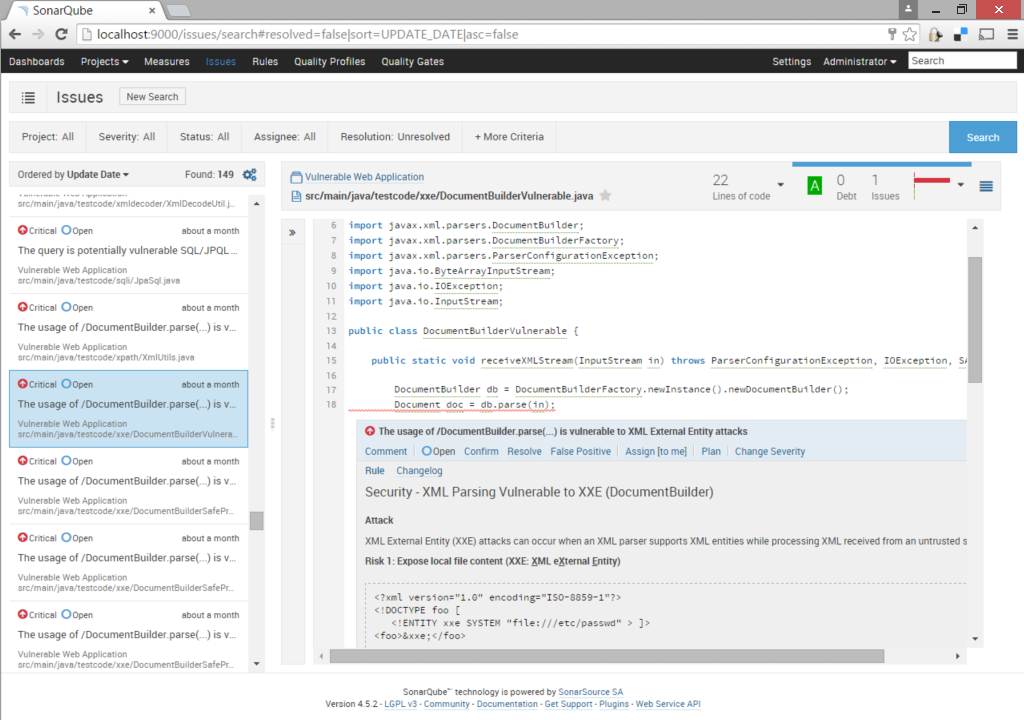
Screenshots
Eclipse
IntelliJ / Android Studio
SonarQube
License
This software is release under LGPL.