Sentry
Enforce security policies.
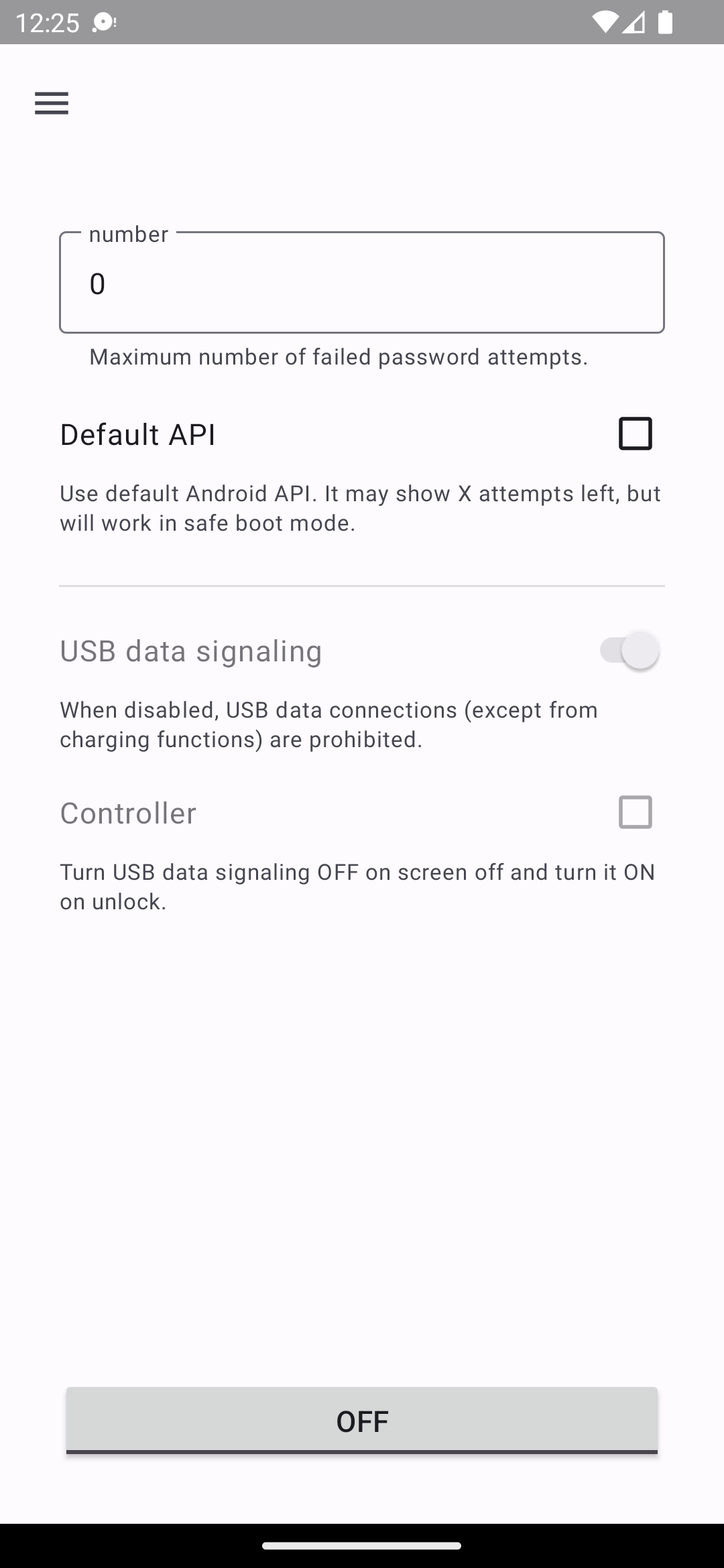
Tiny app to enforce security policies of your device.
It can:
- limit the maximum number of failed password attempts
- disable USB data connections (Android 12, USB HAL 1.3, Device Owner)
Also you can grant it device and app notifications permission to turn off USB data connections automatically on screen off.
Permissions
- DEVICE_ADMIN - limit the maximum number of failed password attempts
- DEVICE_OWNER - disable USB data connections
- NOTIFICATION_LISTENER - receive lock events (optional)
Example
To set as device owner:
$ adb shell dpm set-device-owner me.lucky.sentry/.DeviceAdminReceiver
License
This application is Free Software: You can use, study share and improve it at your will. Specifically you can redistribute and/or modify it under the terms of the GNU General Public License v3 as published by the Free Software Foundation.