OpenSSL on the Android platform. --- The code in this directory is based on $OPENSSL_VERSION in the file openssl.version. See patches/README for more information on how the code differs from $OPENSSL_VERSION. Porting New Versions of OpenSSL. -- The following steps are recommended for porting new OpenSSL versions. 1) Retrieve the appropriate version of the OpenSSL source from www.openssl.org/source (in openssl-*.tar.gz file). Check the PGP signature (found in matching openssl-*.tar.gz.asc file) with: gpg openssl-*.tar.gz.asc If the public key is not found, import the the one with the matching RSA key ID from http://www.openssl.org/about/, using: gpg --import # paste PGP public key block on stdin 2) Update the variables in openssl.config and openssl.version as appropriate. At the very least you will need to update the openssl.version. 3) Run: ./import_openssl.sh import openssl-*.tar.gz 4) If there are any errors, then modify openssl.config, openssl.version and patches in patches/ as appropriate. You might want to use: ./import_openssl.sh regenerate patches/*.patch Repeat step 3. 5) Cleanup before building with: m -j16 clean-libcrypto clean-libssl clean-openssl clean-ssltest 6) Build openssl from the external/openssl directory with: mm -j16 snod && adb sync system If there are build errors, then patches/*.mk, openssl.config, or android-config.mk may need updating. 7) Run tests to make sure things are working: # Run local openssl tests (cd android.testssl/ && ./testssl.sh) # Build and sync libcore tests (croot && cd libcore && mm -j16 snod && adb remount && adb sync) # Run tests from libcore (croot && vogar --classpath out/target/common/obj/JAVA_LIBRARIES/core-tests-support_intermediates/classes.jar --classpath out/target/common/obj/JAVA_LIBRARIES/core-tests_intermediates/classes.jar javax.net.ssl tests.api.javax.net) # Run tests from Harmony (croot && vogar --classpath harmony_tests.jar tests.api.java.math.BigIntegerTest org.apache.harmony.tests.java.math) # try an https website adb shell am start https://online.citibank.com # confirm result in browser The vogar tool can be found externally at http://code.google.com/p/vogar/ Within Google it can be run with ~dalvik-prebuild/vogar/bin/vogar harmony_tests.jar is built from Subversion http://harmony.apache.org/ Within Google it can be found at ~dalvik-prebuild/bin/harmony_tests.jar # You can also run openssl s_server as a test server on the device: adb push ./android.testssl/CAss.cnf /sdcard/CAss.cnf adb shell openssl req -config /sdcard/CAss.cnf -x509 -nodes -days 365 -subj '/C=US/ST=California/L=Mountain View/CN=localhost' -newkey rsa:1024 -keyout /sdcard/server.pem -out /sdcard/server.pem adb shell openssl s_server -cert /sdcard/server.pem -www -verify 1 adb shell am start https://localhost:4433 # confirm result in browser 8) Do a full build before checking in: m -j16 Optionally, check whether build flags (located in android-config.mk need to be updated. Doing this step will help ensure that the compiled library is appropriately optimized for speed and size. To update build flags: a) source openssl.config b) tar -zxf openssl-*.tar.gz c) cd openssl-*/ d) ./Configure $CONFIGURE_ARGS e) examine Makefile and compare with ../android-config.mk f) modify ../openssl.config as appropriate and go to step 3) above. Alternatively, ."/import_openssl.sh import" now prints the post-Configure Makefile for review before deleting in on import.
a version of the official Android openssl setup to build standalone for use in app
Overview
You might also like...

Writeup and exploit for installed app to system privilege escalation on Android 12 Beta through CVE-2021-0928, a `writeToParcel`/`createFromParcel` serialization mismatch in `OutputConfiguration`
Writeup and exploit for installed app to system privilege escalation on Android 12 Beta through CVE-2021-0928, a `writeToParcel`/`createFromParcel` serialization mismatch in `OutputConfiguration`

📱 Android client app for the AryKey 🔑
Android application that prepares an hardware device via USB serial port with a specific password generated deterministically based on three (3) inputs: the App we want to Unlock, the User ID used for login (typically an email address) and the PIN (6 numeric digits) we want to associate with previous inputs.

Appshark is a static taint analysis platform to scan vulnerabilities in an Android app.
Document Index 1.overview 2.startup 3.how to write rules 4.how to find compliance problems use appshark 5.a path traversal game 6.argument 7.engine co
A simple library that can help you detect if you app is modded or tampered with
Android Tamper Detector A simple library that can help you detect if you app is modded or tampered with. This adds a security level that makes it diff
This app should provide a common interface to fetch the estimated time of arrival for parcels
ETA-App This app should provide a common interface to fetch the estimated time of arrival for parcels. It will integrate with several backend systems
Keepass2Android is a password manager app.
Keepass2Android What is Keepass2Android? Keepass2Android is a password manager app. It allows to store and retrieve passwords and other sensitive info
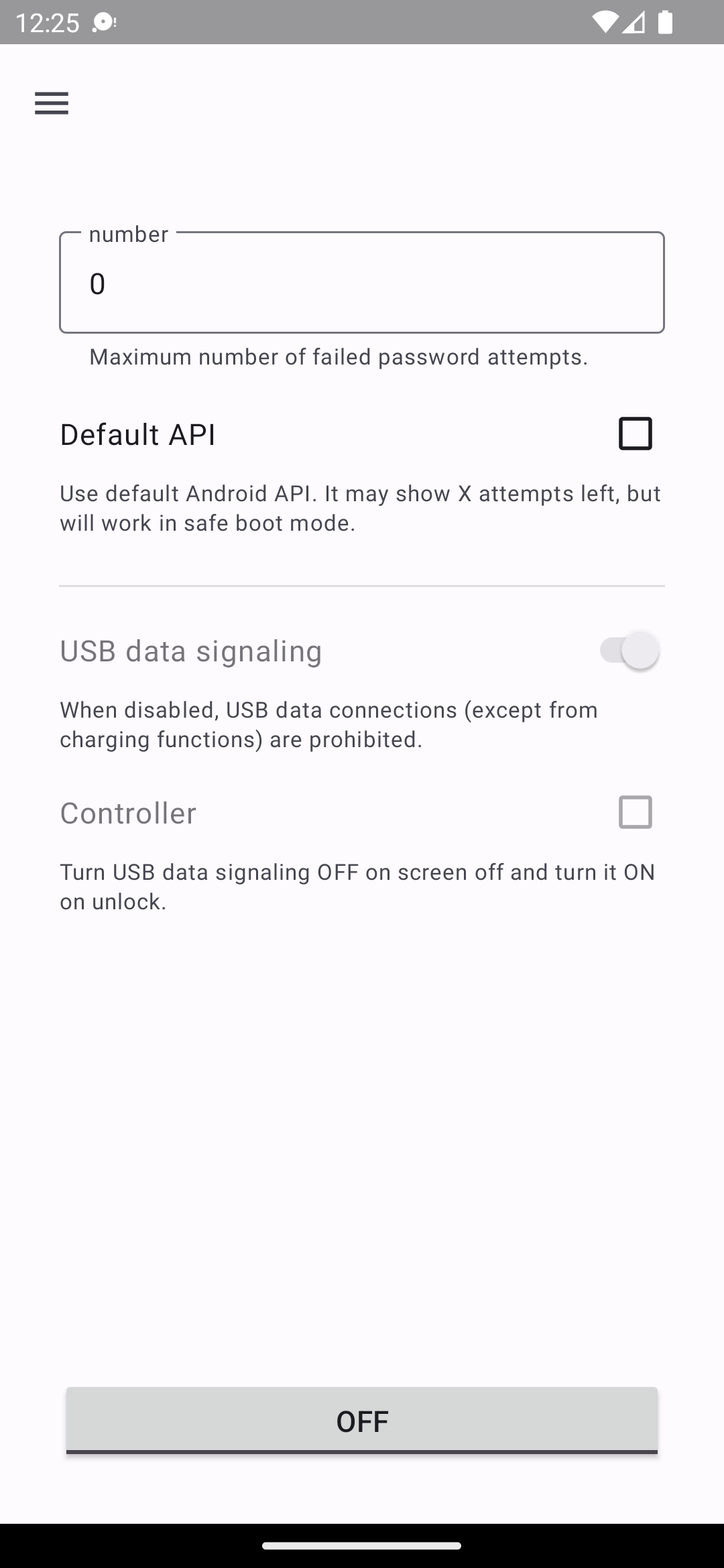
Tiny app to enforce security policies of your device
Sentry Enforce security policies. Tiny app to enforce security policies of your device. It can: limit the maximum number of failed password attempts d

BlackDex is an Android unpack tool, it supports Android 5.0~12 and need not rely to any environment. BlackDex can run on any Android mobile phones or emulators, you can unpack APK File in several seconds.
BlackDex is an Android unpack tool, it supports Android 5.0~12 and need not rely to any environment. BlackDex can run on any Android mobile phones or emulators, you can unpack APK File in several seconds.
backdoor-apk is a shell script that simplifies the process of adding a backdoor to any Android APK file. Users of this shell script should have working knowledge of Linux, Bash, Metasploit, Apktool, the Android SDK, smali, etc. This shell script is provided as-is without warranty of any kind and is intended for educational purposes only.
backdoor-apk backdoor-apk is a shell script that simplifies the process of adding a backdoor to any Android APK file. Users of this shell script shoul
Comments
-
Updated for newer toolchains, 4.4.3 has been deprecated and is not inclu...
opened by AbelCS 0Failed to build with NDK r9d due to forced 4.4.3 toolchain. Removing this line the build process has been completed without errors. So zlib.so not found bug seems to be resolved for newer NDKs.
-
Now it will build as a subproject. (It will also
opened by FellowTraveler 1continue to work building as the main project.) I also added libssl_static. I also removed -ldl for libcrypto_static since it's ignored anyway and was causing a warning.
Signed-off-by: FellowTraveler F3llowTraveler@gmail.com
-
make it work with new ndk
opened by dongshengbc 0if you try to compile it with latest ndk (r8d), it failed with following error like this:
ndk/build/gmsl/__gmsl:512: *** non-numeric second argument to `wordlist' function: ''. Stop.
this patch will fix it.
This project is an Android Studio plugin version of BlackObfuscator
This project is an Android Studio plugin version of BlackObfuscator, it supports obfuscating code automatically. More information about this project are in BlackObfuscator.
ZRoot is a library that makes it easy to use root on Android, such as calling system service with root privilege.
ZRoot is a library that makes it easy to use root on Android, such as calling system service with root privilege. Usage See sample or user guide
MiHawk 🦅👁️ is simple and secure 🔒 Android Library to store and retrieve pair of key-value data with encryption , internally it use jetpack DataStore Preferences 💽 to store data.
MiHawk MiHawk ?? ??️ is simple and secure ?? Android Library to store and retrieve pair of key-value data with encryption , internally it use jetpack
Xposed OneLineClock - Always use one line clock on Android 12 lock screen
Xposed OneLineClock - Always use one line clock on Android 12 lock screen
Easy to use cryptographic framework for data protection: secure messaging with forward secrecy and secure data storage. Has unified APIs across 14 platforms.
Themis provides strong, usable cryptography for busy people General purpose cryptographic library for storage and messaging for iOS (Swift, Obj-C), An
This app will show grid overlay over whole system which helps you to verify your excellent app design.
GridWichterle for Android This app will show grid overlay over whole system which helps you to verify your excellent app design. Download: What is the
Analyze any Android/Java based app or game
ClassyShark Introduction ClassyShark is a standalone binary inspection tool for Android developers. It can reliably browse any Android executable and
A android app for encrypting apk
A android app for encrypting apk
A simple android app that parses its own signature and displays it
SigDisplayer Usage Download the release APK or clone the repository and compile yourself. Sign the APK with your preferred keystore. Install and open
Android app to test various cryptography algorithm.
CryptographyLesson Introduction This android app shows how cryptographic algorithm works. You can encrypt or decrypt messages and try different algori